Archive | InBrief
Is your utility prepared for industroyer malware?
Is your utility prepared for industroyer malware?
While electric grid operators in the USA are required to meet cyber security requirements in NERC CIP and implement guidelines such as NISTIR 7628, compliance with the regulation does not automatically imply total security. Additionally, this level of security and compliance focus has not been applied to other utility services, such as water and gas networks. Recent security research regarding a 2016 cyber-attack on Ukraine’s power grid demonstrates how malicious actors are becoming more sophisticated, and have the capability to impact all manner of utility operations when security is not properly implemented.
In December 2016, attackers were successfully able to use a new malware framework to cause a power outage in and around the Ukrainian capital of Kyiv. During one of the coldest months of Winter, the attackers were able to cut power, and thus heating, to a significant number of Ukraine residents. Recently published research estimates that the malware made its way into the utility network approximately six months prior to the power outage using a spear phishing (e-mail) campaign. While this is not the first cyber-attack in Ukraine to result in a power outage, the level of sophistication in the malware’s design and targeting capabilities is unprecedented. The sophisticated malware package, known variously as ‘Industroyer’ or ‘Crash Override’, has a modern, modular design framework, and includes support for various Industrial Control System (ICS) protocols, such as IEC 61850, and targeted vulnerability exploits for Siemens SIPROTEC devices, which are known to be used in Ukraine's power distribution systems.
What do we know?
The Industroyer malware is reportedly the first malware framework designed and deployed with the specific intent on causing harm and disruption to utility SCADA/ICS networks. Researchers reported that the malware reviewed had capabilities to utilize prominent ICS protocols used for monitoring and controlling remote equipment, including OPC DA, IEC 60870-5-101, IEC 60870-5-104, and IEC 61850, which are commonly used in European and non-US grid systems. However, the most notable capability of the malware framework is its ability to be easily extended to support other protocols, such as DNP3, which is commonly used in US utilities for device communications and control operations. The malware framework may also be repurposed to attack other ICS infrastructures, such as local water or gas utilities, manufacturing systems, or oil and gas distribution.
How could this occur within the utility or in other utility companies?
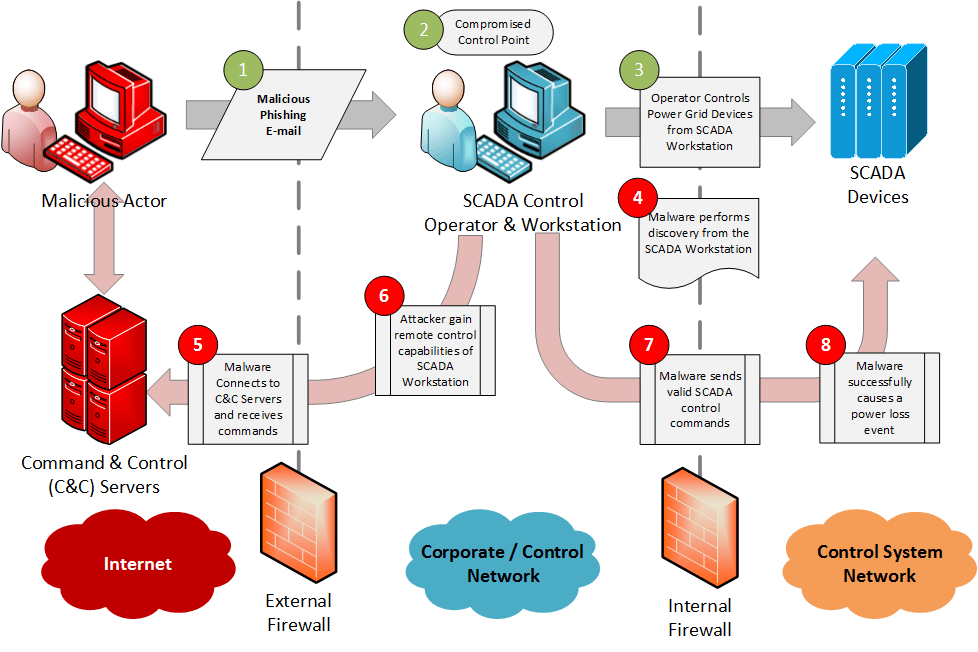
Figure 1: Sample Attack Kill Chain The diagram above provides an overview of how this attack was likely carried out against Ukraine’s power grid. This attack kill chain is common amongst most malware packages and is applicable to other utility organizations. Let’s break down how this attack kill chain was successful:
-
A malicious actor sends a spear phishing e-mail with a malicious malware package attached or linked to a targeted individual or set of individuals based on social research or engineering.
-
The target of the phishing e-mail, in this case a SCADA operator, opens the phishing e-mail and opens the malware from their SCADA control workstation. The malware installs itself on the workstation and continues to operate quietly in the background undetected by the operator.
-
The SCADA operator continues work as usual, it is estimated that the time between the time of install (#2) and time of attack (#7) was approximately six months.
-
The malware, quietly in the background, performs discovery of the local corporate network and on the control system network with the intention of identifying desired SCADA systems to potentially exploit.
-
After installation, the malware is programmed to establish a line of communication back to a system operated by the attacker, referred to as a Command & Control (C&C) server, which resides on the public Internet.
-
Once C&C communications is established, the attacker gains bi-directional communications to/from the SCADA operators workstation. The attacker is then able to remotely interact with the SCADA workstation and locally accessible networks including the corporate and control system networks. When the attacker decides to execute their attack, commands are sent to the malware package for either immediate execution, or scheduled for a future date.
-
Once triggered by the attackers, the malware sends SCADA/ICS control commands to the SCADA devices in the field to shut power off. To the SCADA field devices, these commands appear legitimate, conform to the necessary specification, e.g. IEC 61850, and are received from an authorized system.
-
The SCADA devices in the field, acting upon what appear to be valid and authorized control commands, execute the commands sent by the malware and cause a power outage event.
What does this mean and what can we do?
The attack on Ukraine’s power grid used a very sophisticated malware package, the methods used to initiate the attack are well known and common in many types of malware. Security researchers have indicated that the malware made its way into the power grid network through a spear e-mail phishing campaign. Even with the advent of new prevention and detection technologies, e-mail phishing campaigns remain highly successful, due to their low cost of execution, low risk of attribution, and the inevitable timing gap between the disclosure of vulnerabilities, and the patching of vulnerable machines. In the case of the Ukraine power grid attack, there are indicators that several common security controls were either not present in the network, or failed to act as intended:
-
Restricting network access: The SCADA operator workstation could access the Internet, and was not prevented from connecting to untrusted systems, e.g. the anonymous Tor network. The same machine may have been able to open e-mails as well, which allowed the malware to execute, establish command & control connectivity and receive commands and updates from the attackers' staging servers.
-
Application whitelisting: The e-mail phishing attack allowed execution of untrusted (attackers') code on the compromised workstation.
-
Restricting user privileges: The SCADA operator’s user account could execute and install untrusted (attackers') code through explicit or unrestricted permissions. Such permissions are typically only provided to local workstation administrators
-
Anti-malware defenses: The malware was not detected by host anti-virus software, which is likely due to signature-based method of most anti-virus software today.
-
File integrity monitoring: The endpoint protection software also did not detect that the malware made modifications to the Windows Notepad application to inject a malicious backdoor.
-
System patching and updates: The malware contained a module designed to exploit a denial-of-service vulnerability in Siemens SIPROTEC devices that was discovered in 2015. If executed, a network intrusion detection and/or prevention system (IDS/IPS) configured with the corresponding signature would have triggered an alarm and potentially prevented a subset of the attack.
-
Network intrusion detection and prevention: The malware was not detected by network-based intrusion detection systems as it performed a network system and port scan across the control system network.
It is easy to play the armchair critic, and second guess the security implementation of Ukrainian power plants. Nonetheless, it is a reality that even when good security controls are fully implemented, in any environment, controls can fail or be disabled temporarily when operational demands take precedence. This incident serves as an example of why a defense-in-depth strategy, with overlapping and complimentary layers of security, is critical to ensuring that the organization is more secure and better prepared in the event of an attack. Such an approach requires blending preventative controls, which could interrupt steps (1) and (2) of the kill chain, with detective controls, which might have identified the intrusion during steps (3) thorough (8). When combined with a strong incident response capability, this blend of preventative and detective controls can enable you to minimize the likelihood of an intrusion, identify active intrusions, and respond to security events in a coordinated and impactful manner. If you’d like to speak to one of our Cybersecurity specialists to discuss how malware attacks may affect your organization, reach out.
Related Articles / References: